
how tokenization and encryption are used to protect you against them.
Introduction
In the fast-evolving realm of data security, two titans currently dominate this space enhanced by the latest technological developments: Tokenization and Encryption. As organisations strive to safeguard information, comply with data protection regulation and win the trust of the public at large, knowing which method to back remains the holy grail of security. In this article we set out an overview of tokenization vs. encryption, and go on to examine their strengths, weaknesses through case studies, and ultimately, their ability to protect against the growing threat of cyber-attacks.
Exploring the All-Time Biggest Online Data Breaches in 2023
The most significant data leakage, as at the time of writing this article, was the data breach that occurred in March 2020 on Cam4. This breach resulted in the exposure of more than 10 billion data records. Following that, the second-largest data breach in history was the Yahoo data breach in 2013. Initially, the company reported about one billion exposed data records. However, after conducting an investigation, the number was updated, revealing that a staggering three billion accounts were affected. Another notable data leakage event was the security breach of India’s national ID database, Aadhaar, in March 2018. In this breach, over 1.1 billion records were exposed, including sensitive biometric information like identification numbers and fingerprint scans. This information has the potential to be misused for unauthorized purposes such as opening bank accounts or accessing financial aid and various government services. 1
The grave danger of these sort of breaches lie in our inextricable dependence on technology as a fundamental tenant of what it currently means to be human. As humanity embeds itself into the digital era, corporations and governments around the world have progressively intensified their reliance on technology for the purpose of gathering, examining, and safeguarding personal data. Consequently, a surge in cyber-crimes has taken place, encompassing both minor violations and large-scale attacks affecting billions of users.
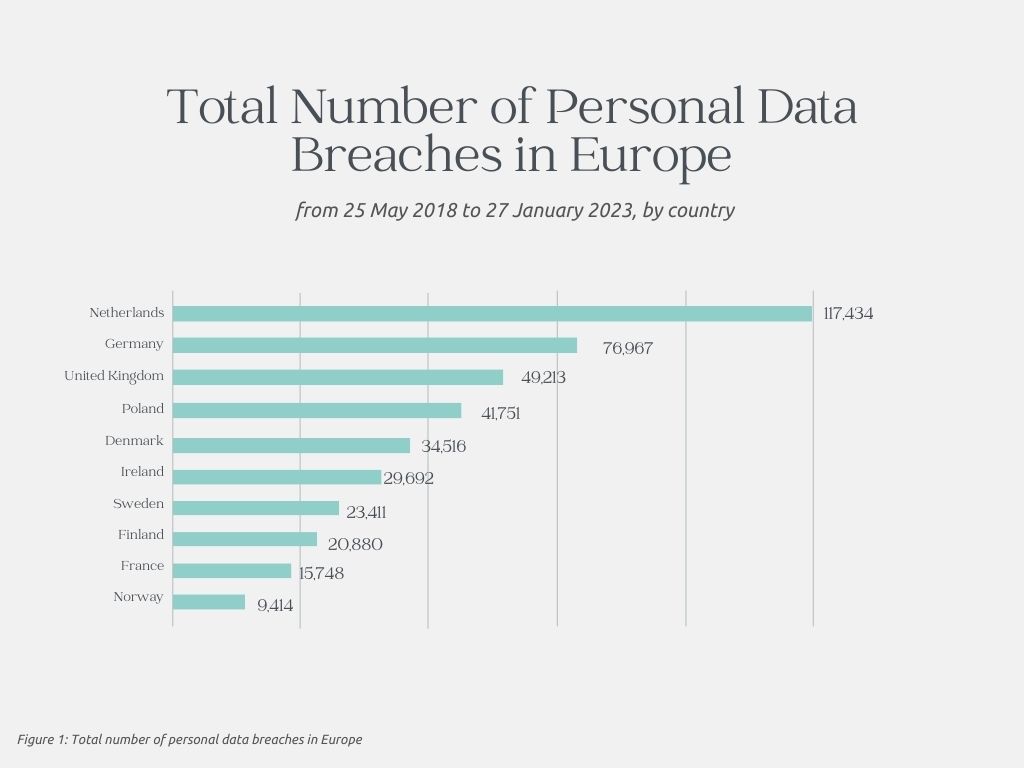
Since the General Data Protection Regulation (GDPR) implementation Europe-wide on the 25th of May 2018, the highest number of personal data breaches as of January 2023 were reported in the Netherlands, a total of around 117,434. Germany ranked second, with more than 76,000 personal data breach notifications. 2
The Expensive Reality of Data Protection
As of 2022, the median expense of a solitary data breach across all industries worldwide reached approximately $4.35 million USD. This proved to be most exorbitant in the healthcare sector, as every disclosed breach inflicted a substantial financial burden of $10.1 million USD upon the affected party. The financial segment closely followed suit, with each breach resulting in a loss of around $6 million ($1.5 million higher than the global average).
Cybercriminals carefully select their targets by considering two key factors: the potential for maximum impact and the possibility of achieving maximum profit. Financial institutions align perfectly with these conditions due to their storage of highly valuable data. Furthermore, the ongoing digital transformation initiatives undertaken by these institutions present even greater opportunities for cyber attackers to gain unauthorised access to this coveted data. 3
Equifax Data Breach
How did the data breach occur?
The occurrence of the data breach is a matter worth examining. The Equifax data breach can be properly characterized as a catastrophic event. The presence of a series of woeful cybersecurity practices rendered the security breach alarmingly effortless for cybercriminals to exploit. Identifiable are four fundamental vulnerabilities that significantly contributed to the compromise of security.
- The company did not adequately address a well-known vulnerability (CVE-2017-5638) in its Open Source development framework, Apache Struts. Despite the patch for CVE-2017-5638 being available for 6 months, it was not applied, leading to the breach.
- Equifax, on the other hand, failed to implement proper segmentation in its ecosystem, allowing the attackers to seamlessly navigate through multiple servers once they gained access through the web portal breach.
- Further compromising Equifax’s security, the hackers discovered usernames and passwords stored in plain text. Exploiting this security flaw, they were able to elevate their privileges and gain deeper access to sensitive information.
- To make matters worse, Equifax’s negligence extended to failing to renew an encryption certificate for one of their internal tools. This oversight enabled the hackers to exfiltrate data without detection for several months.
In addition to these circumstances, it should be noted that over a month had transpired before Equifax ultimately disclosed the breach to the public. Throughout this duration, high-ranking executives engaged in the sale of company stocks, thus leading to allegations of insider trading.
What specific data had been compromised in this incident?
The Equifax data breach had the potential to affect more than 40% of the American population.
The following data was compromised:
- Names
- Dates of birth
- Social security numbers
- Driver’s license numbers
- Credit card numbers
Due to the highly sensitive nature of Personally Identifiable Information (PII) and financial information that was compromised, Equifax was fined $700 million for the breach.
Lessons from the Equifax Data Breach:
Financial service firms and small businesses can derive significant lessons from this breach.
1. Data Sensitivity Awareness:
Lesson: It is imperative for companies to exhibit a profound understanding of the sensitivity associated with the data they gather, store, and manipulate, particularly in the case of personally identifiable information (PII) encompassing social security numbers, addresses, and financial data.
Action: Establish a comprehensive data classification system that is capable of categorizing information effectively. Additionally, employ encryption techniques to safeguard sensitive data and enforce stringent access controls.
2. Patch Management:
Lesson: Unaddressed software vulnerabilities represent a frequent point of entry for malicious hackers. The Equifax breach transpired as a result of an unaddressed Apache Struts framework.
Action: Consistently update and address any software and systems through the implementation of vulnerability management tools to promptly detect and resolve weaknesses.
3. Network Security:
Lesson: Inadequate network security measures can result in unauthorized access to critical systems.
Action: Employ firewalls, intrusion detection systems, and encryption protocols. Regularly evaluate network security and perform penetration testing.
4. Incident Response Plan:
Lesson: Equifax received criticism for its insufficient response following the discovery of the breach.
Action: Create a comprehensive incident response plan that includes clear communication channels, defined roles, and specified responsibilities. Conduct regular drills and continuously update the plan based on acquired knowledge.
5. Authentication and Access Control:
Lesson: The risk of unauthorized access can arise from weak or stolen credentials.
Action: It is imperative to implement robust authentication mechanisms such as multi-factor authentication. Additionally, enforce the principle of least privilege, ensuring that employees are granted the minimum level of access required for their respective roles.
6. Vendor Risk Management:
Lessons Learned: The breach at Equifax occurred as a result of a vulnerability in software provided by a third party.
Recommended Action: It is crucial to regularly evaluate and monitor the security practices implemented by third-party vendors. Additionally, it is advisable to incorporate stringent security clauses in contracts and agreements.
7. Data Encryption:
Lesson: Encrypted data presents a significant deterrent against misuse, even in the event of unauthorized access.
Action: Implement encryption measures for data at rest and during transmission. It is imperative to establish proper management and protection protocols for encryption keys.
Demystifying Tokenization: How It Works and Why It Matters
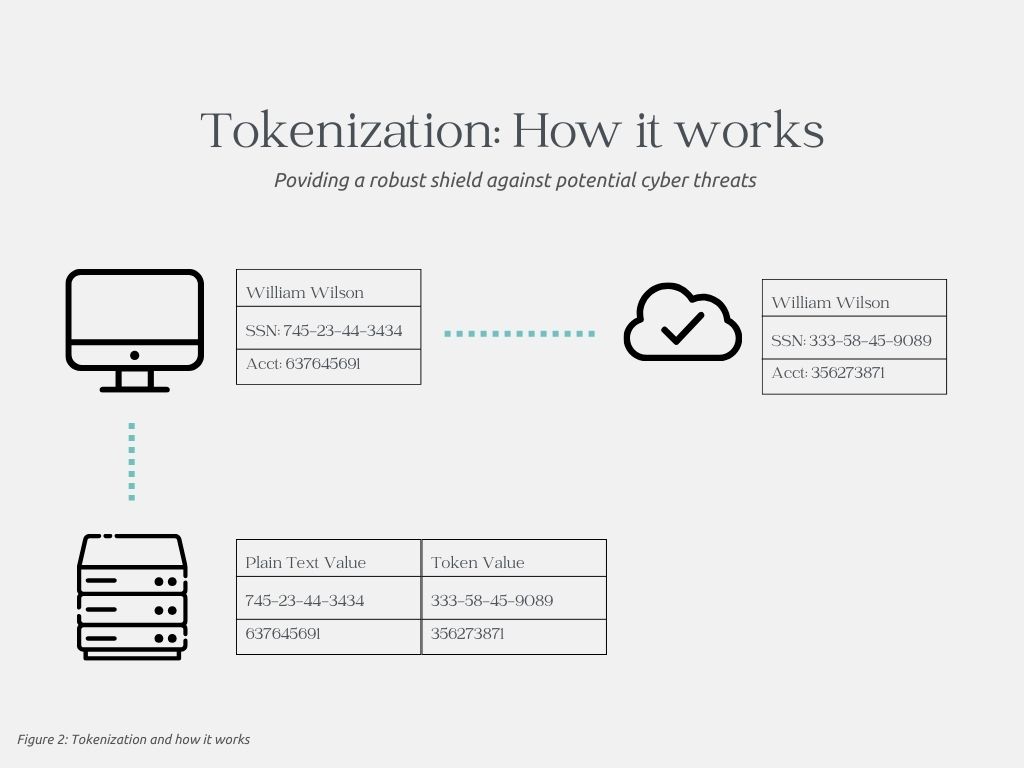
Tokenization is a crucial data security technique that has gained significant importance in today’s digital landscape. By carefully substituting sensitive information with non-sensitive tokens, this process provides a robust shield against potential cyber threats.
Essentially, when sensitive data like credit card numbers or personal identification numbers (PINs) are tokenized, they are replaced with placeholder tokens that bear no resemblance to the original data. This technique is exceptionally effective in reducing the exposure of sensitive information, making it significantly harder for malicious actors to compromise it. Tokenization plays a vital role in safeguarding sensitive data, ensuring that individuals’ financial and personal information remains secure. For example, if a credit card number is “1234-5678-9876-5532” it is then replaced with a unique token “abc123xyz456pqr789”. This token is meaningless to anyone who might intercept it, but the payment processing system can use it to reference the actual credit card information securely stored in a database. Below we set out what tokenization true impact may be and how it works and why it matters in today’s data-driven world.
The Power of Encryption: How It Works and Why It Matters
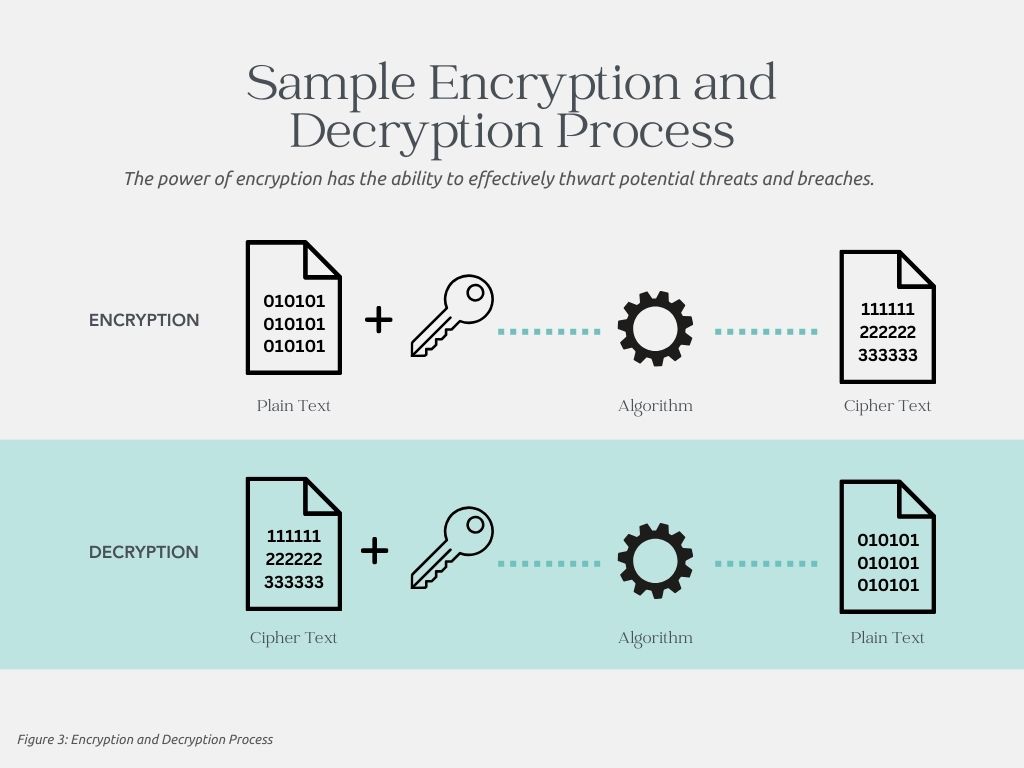
Encryption plays a pivotal role in maintaining the security of sensitive data. Unlike Tokenization encryption is primarily used to secure data during transmission or storage. It scrambles the original data into a ciphertext using an encryption algorithm and a secret key. The ciphertext can be decrypted back to the original data using the appropriate decryption key. Encryption is reversible, meaning that the data can be decrypted back to its original form if you have the correct decryption key. For example, converting the word “HELLO” into a random set of characters like “8d78evf”
By transforming information into an unreadable format, it prevents unauthorized access without the necessary decryption key or password. This fundamental technique is widely employed in information security, providing protection for data stored, transmitted, and processed. Whether it’s safeguarding personal details, financial transactions, or confidential business information, encryption ensures that sensitive data remains secure throughout its lifecycle. The power of encryption lies in its ability to effectively thwart potential threats and breaches, giving individuals and organizations peace of mind and confidence in their digital interactions.
Essentially, when sensitive data like credit card numbers or personal identification numbers (PINs) are tokenized, they are replaced with placeholder tokens that bear no resemblance to the original data. This technique is exceptionally effective in reducing the exposure of sensitive information, making it significantly harder for malicious actors to compromise it. Tokenization plays a vital role in safeguarding sensitive data, ensuring that individuals’ financial and personal information remains secure. For example, if a credit card number is “1234-5678-9876-5532” it is then replaced with a unique token “abc123xyz456pqr789”. This token is meaningless to anyone who might intercept it, but the payment processing system can use it to reference the actual credit card information securely stored in a database. Below we set out what tokenization true impact may be and how it works and why it matters in today’s data-driven world.
Comparison of Tokenization and Encryption
Data security has become a critical issue in the digital era, leading to the rise of two reliable methods to protect sensitive data: tokenization and encryption. With their unique approaches, both techniques aim to defend valuable information against unauthorized access and cyber threats. Tokenization involves substituting sensitive data elements with non-sensitive placeholders, known as tokens, rendering them meaningless if intercepted. Conversely, encryption employs complex algorithms to transform readable data into an incomprehensible format, requiring a deciphering key to retrieve the original information. While both methods offer robust security measures, they differ in their implementation and level of protection. To determine which reigns supreme in the battle of data security, it is crucial to delve deeper into the strengths and limitations of tokenization and encryption.

What’s the future of Tokenization and Encryption?
The global tokenization market size was valued at $2.39 billion in 2022 & is projected to grow from $2.81 billion in 2023 to $9.82 billion by 2030. 4 While the global encryption software market size was valued at USD 13.46 billion in 2022 and is projected to expand at a compound annual growth rate (CAGR) of 16.2% from 2023 to 2030. 5
Before the rise in popularity of tokenization, encryption was the favored method for ensuring compliance. However, we have already witnessed the advantages and drawbacks of this approach. The primary concern lies in its substantial cost. Encryption necessitates robust data systems capable of performing the complex calculations required for advanced encryption.
This presents a greater challenge for smaller merchants who have limited financial resources. In order to secure their data, smaller merchants may be required to undergo a substantial system upgrade.
The tokenization market is experiencing significant growth as more individuals utilise digital wallets, online banking, and e-commerce platforms. This surge in demand for secure digital payment methods, in addition to the requirement to comply with PCI DSS (Payment Card Industry Data Security Standard) regulations which safeguard customer payment information, and the escalating incidence of financial fraud in e-commerce, has further strengthened the market. Adoption of tokenization not only ensures the protection of sensitive payment data, but also presents businesses with fresh opportunities to explore in the constantly evolving digital landscape.
Moreover, the increasing preference for payment apps across multiple industry verticals is expected to create significant opportunities for the tokenization market. From retail to healthcare, more businesses are incorporating payment apps into their operations, offering convenience and flexibility to their customers. Tokenization addresses the concern of storing and transmitting payment data securely, making it an ideal solution for these industry verticals.
Conclusion
When it comes to safeguarding data in cloud services or applications, it is essential to understand the benefits and limitations of tokenization vs encryption. Both methods offer their own strengths in protecting sensitive information and complying with legal regulations.
Encryption is a powerful technique that transforms data into an unreadable format, ensuring its confidentiality. However, it may introduce some complexities, such as key management and potential vulnerabilities. On the other hand, tokenization replaces sensitive data with non-sensitive tokens, minimising risks while maintaining usability. Nevertheless, it may not be suitable for all scenarios.
Organisations must carefully evaluate their specific use cases and legal requirements to determine whether to utilise encryption, tokenization, or a combination of both. Considering factors like data sensitivity, access control, and compliance, organisations can customise their data protection strategies accordingly.
At Aspect Advisory we use a combination of both methods to maximise data protection, taking advantage of tokenization’s data segmentation benefits and encryption’s comprehensive data security. The choice between these approaches is based on client’s business model needs and specific security requirements, regulatory compliance, and the nature of the data being protected.
References:
- All time biggest online data breaches 2023: https://www.statista.com/statistics/290525/cyber-crime-biggest-online-data-breaches-worldwide/
- Personal data breaches in Europe 2023: https://www.statista.com/statistics/1203667/total-personal-data-breaches-europe/#:~:text=Since%20the%20General%20Data%20Protection,76%2C000%20personal%20data%20breach%20notifications
- 10 Biggest data breaches in Finance: https://www.upguard.com/blog/biggest-data-breaches-financial-services
- The global tokenization market size by 2030: https://www.fortunebusinessinsights.com/tokenization-market-107201
- The global encryption software market size by 2030: https://www.grandviewresearch.com/industry-analysis/encryption-software-market#:~:text=The%20global%20encryption%20software%20market,Device%20(BYOD)%20among%20enterprises.
Contact us

Stuart Thomson
Partner,
Aspect Advisory
![]()
